What are proxy servers and how do people use them?
1Click VPN Team in cybersecurity
07.12.2023 | 4 min read

Table of contents
Proxy servers allow users to access the internet from their home or office whilst hiding their location, IP address, and identity.
But what are the uses for proxy servers? How are they different from VPNs? Keep on reading to learn everything there is to know about proxy servers.
What are the Main use cases for proxies?
There are two main methods of accessing the internet whilst keeping one’s identity and location hidden; either by using a virtual private network (VPN) or a proxy server, – although many VPN providers also make proxies available, depending on any customer requirements.
Large organizations tend to use a pool of proxy servers to access the web for a variety of reasons, mainly to do with the ability to ‘scrape’ the contents of websites and to facilitate geographically targeted search engine optimization campaigns. However small businesses with just a couple of employees and private individuals often use a combination of a VPN and a proxy server in conjunction, either as a belt and braces security approach, or because a proxy makes more sense for their activities.
What’s the difference between a proxy and a VPN?
Both proxy servers and VPNs can help beef up users’ online privacy and security, but they work in different ways and carry distinct features and benefits, depending on the user’s purpose.
Proxies exist as third-party servers, sitting between a person’s home or office router and the wider internet. Just like a VPN, they can be used to protect anonymity, control access to the internet from an office or household, and filter content, perhaps in a school or a domestic environment where there are children and content blockages need to be put in place.
VPNs can perform a similar service to proxies, but additionally, their connection to the internet is made by an encrypted ‘tunnel’. Some proxies can also provide encryption, but if so, it is often limited to certain types of traffic, for example, secure web browsing using the HTTPS protocol (hypertext transfer protocol secured). However, proxies like SOCKS5 (SOCKS meaning ‘secure sockets’) is a network protocol that allows communication with servers via a firewall. Standard HTTP proxies do not usually encrypt data at all.
VPNs route all their internet traffic through their encrypted servers, including file transfer protocol (FTP), web browsing and email communications. Proxies, however, only route specific types of traffic, such as web browsing or specific pre-sanctioned application data.
A moving or a static target
A VPN offers better protection from hackers due to its encryption and the large number of servers available via a VPN’s network internationally. However, proxies are usually single servers located in fixed predetermined locations. When a user connects to a website via a proxy, the target website identifies the IP address of the proxy server rather than the user’s actual IP address. This can help protect your identity and location. Some people prefer the proxy as opposed to the VPN if the work they are doing online means that their IP address remains static, as opposed to changing each time when they log on to the web via a VPN.
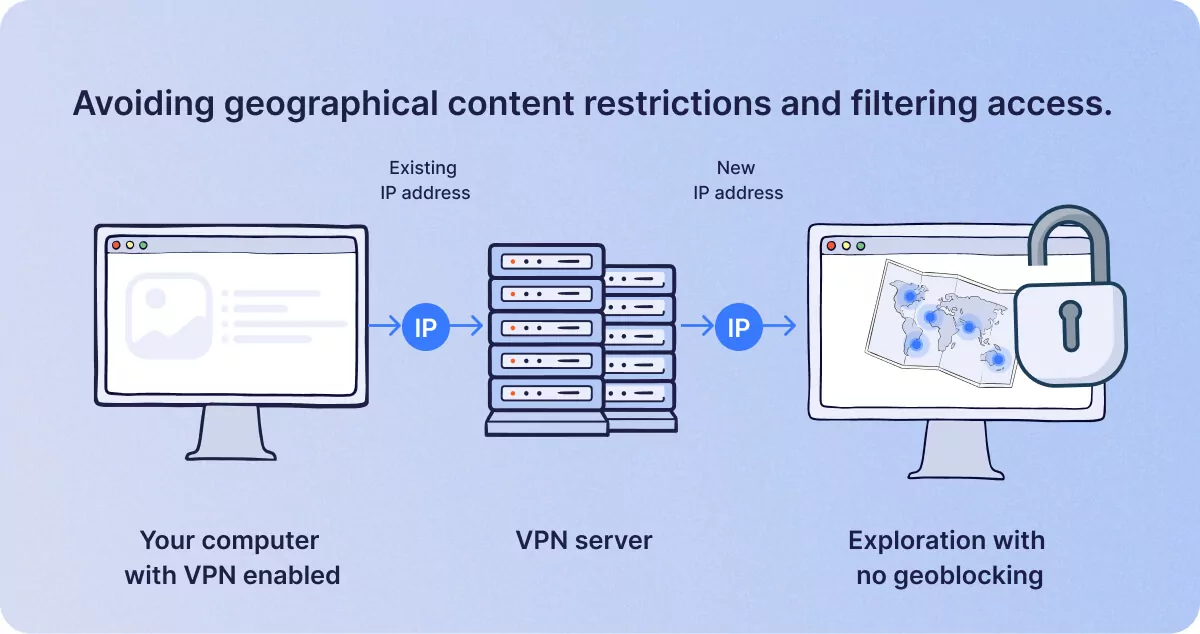
Avoiding geographical content restrictions and filtering access.
Whilst both VPNs and proxies can circumvent content restrictions, such as accessing Netflix in the USA when the user is traveling in Europe; proxies are better at restricting outgoing access from a given household or office than a VPN. For example, a concerned parent with young children might well use a proxy to specify no connections allowed to a given website or platform such as Tinder or any adult film sites. With a proxy, a user can specify certain websites that can’t be accessed via the household router, which is better for parental controls. Proxies are sometimes used in schools for this purpose, often to prevent schooltime access to social media, which is why some crafty pupils use their own VPN software to get around the restriction.
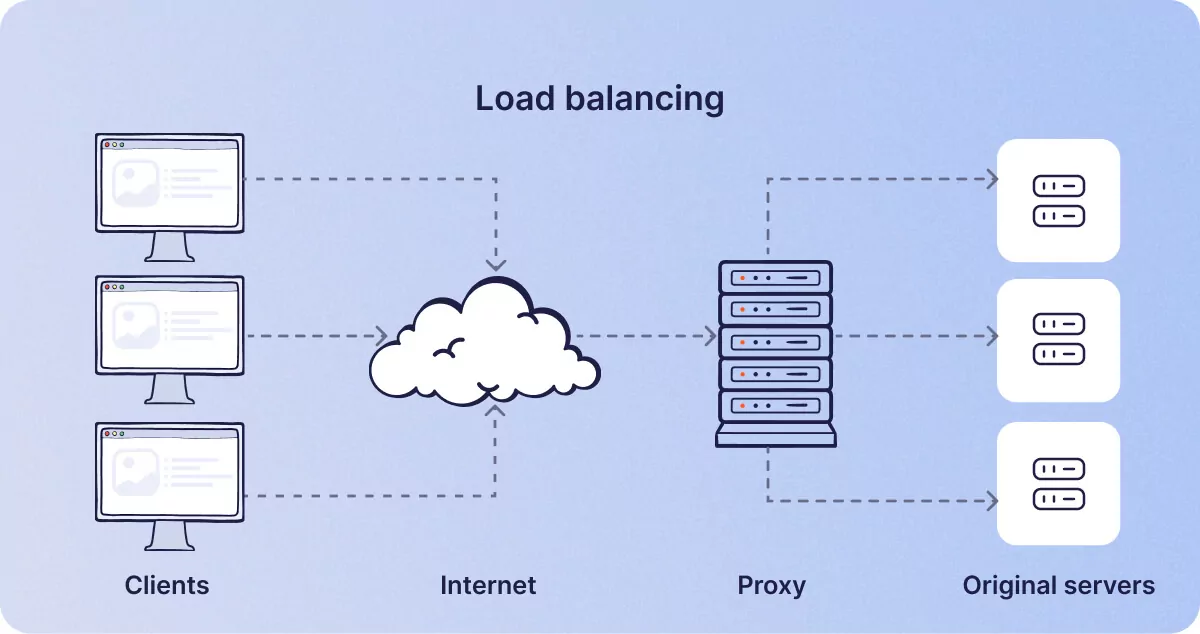
Load balancing
No, this is nothing to do with ensuring that all the boxes on your car’s roof rack are securely tied down! Some small businesses or data-hungry freelance knowledge workers can sometimes use proxy servers to spread network traffic evenly across multiple proxies. If a lot of data is being transferred and the process is causing slow network traffic, sharing the load across three or four proxy servers for different applications can speed up workflow considerably.
For example, in a small business or a sole trader’s office, Photoshop files might be transferred via one proxy server, video clips by another, whilst the family’s gaming and TV streaming in the rest of the building can be routed by another proxy. In short, you can split the traffic out of one household or small business into several less clogged-up streams.
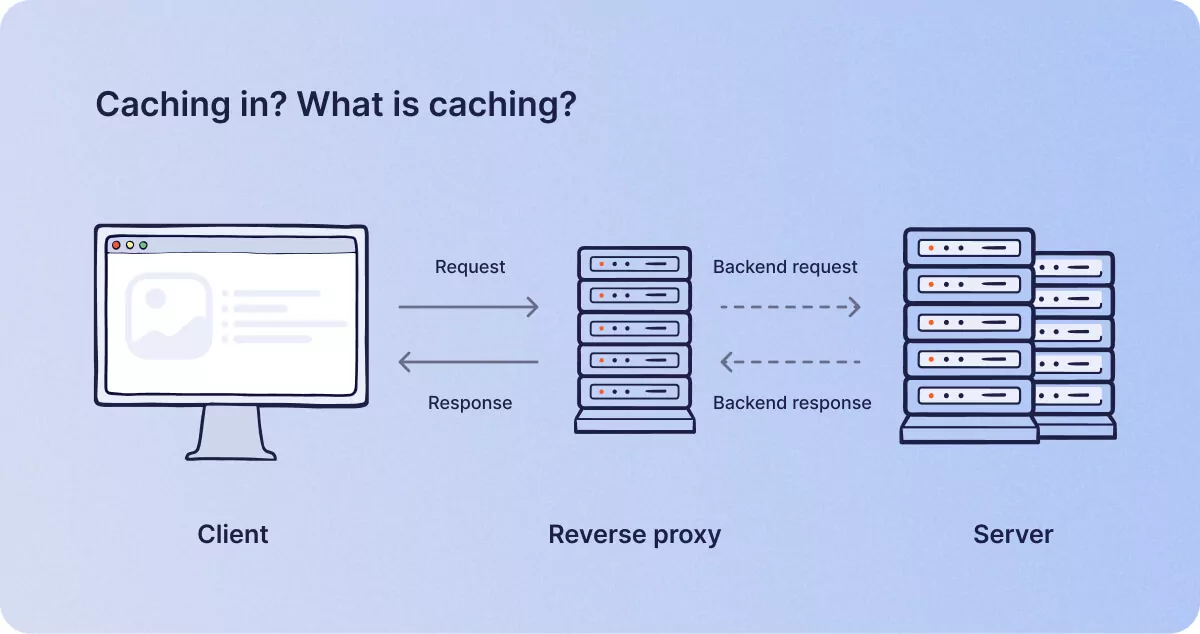
Caching in? What is caching?
You might be forgiven for thinking that caching web pages was related to financial transactions in hard currency; but ‘caching’ refers to the practice of storing frequently visited web page files onto a proxy server, so that they can be loaded very quickly without having to wait for the files to download from the target server every time they are requested by a browser.
This function can’t be performed on a VPN, so some people might experience increased speeds when accessing familiar websites. But the only drawback to this system is the necessity to refresh the cache regularly, or a visitor could end up loading an historical version of a web page and missing out on any fresh content that might have changed since their last visit.
This is why, when sometimes logging onto an online bank or e-commerce website where you might hold an account means that you have to empty your cache and cookies if logging on seems problematic.
Proxy servers can also be used by the baddies.
As a proxy server can mask one’s location and identity, they can also be used for nefarious purposes by the very people that VPNs are built to protect us from. As a result, some websites have long lists of servers that have previously been identified as proxies, and some can block access from those specific IP addresses. It is more difficult for websites to keep logs of VPN servers, so it’s easier for some companies and institutions to block proxies than to try to block access to VPNs.
Horses for courses
There’s really no ‘one size fits all’ approach when deciding to use either a VPN, a proxy server, or a combination of both. Users should take stock of all the online activities they undertake, then decide whether the home or business use cases make sense to take one route or another.
Obviously, large businesses have whole IT departments and educated professionals to deal with these issues, whereas most self-employed sole traders or private individuals will have very different needs from big business. In short, if it saves time, enhances security and does what you need it to do, then so long as you have some sort of system in place, it’s better than simply ignoring the issue and hoping any IT based problems will simply go away.
Similar posts

Proxy Vs. VPN: What’s the Difference?
In an increasingly digital world, online privacy has become a major concern for Internet users the world over. As a resu…

Staying Secure Online: 7 Tips for Safely Using Public Wi-Fi
The Internet is an essential part of virtually everything we do nowadays, from shopping to banking to entertainment, and…